If you’re a contractor or subcontractor working with the Department of Defense (DoD), chances are you’ve heard about CMMC 2.0. If your company works on DoD contracts and handles Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), you need to be CMMC compliant.
In a previous post Practical Guide to CMMC Compliance, we covered the basics of CMMC 2.0. Now, let’s focus on what you should do now to prepare for a CMMC assessment. A quick recap of how to figure out which level applies to your business:
Which CMMC Level Applies to Your Business?
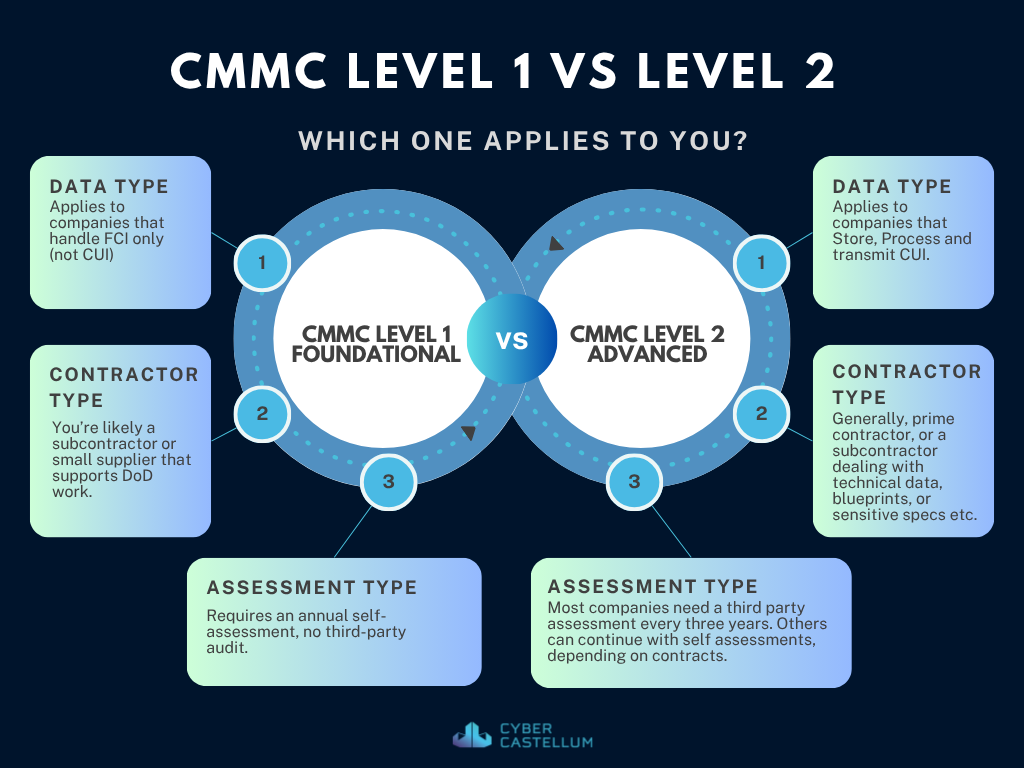
CMMC Level 1 – Foundational
- Applies to companies that handle FCI only (not CUI).
- You’re likely a subcontractor or small supplier that supports DoD work.
- Requires an annual self-assessment, no third-party audit.
CMMC Level 2 – Advanced
- Required for companies that create, receive, store, or transmit CUI.
- You might be a prime contractor, or a subcontractor dealing with technical data, blueprints, or sensitive specs etc.
- Some companies will need a third-party assessment every three years; others can continue with self-assessments, depending on how “critical” their contracts are.
Not sure what kind of data you handle? Check your contracts or reach out to your contracting officer. It’s better to confirm now than scramble later.
Whether you’re aiming for Level 1 or Level 2, preparation is key. Below is a checklist to help you get ready for your CMMC assessment—without losing sleep (or valuable contracts).
CMMC Readiness: Basic Cyber Hygiene Practices

These are basic but essential practices required for CMMC readiness:
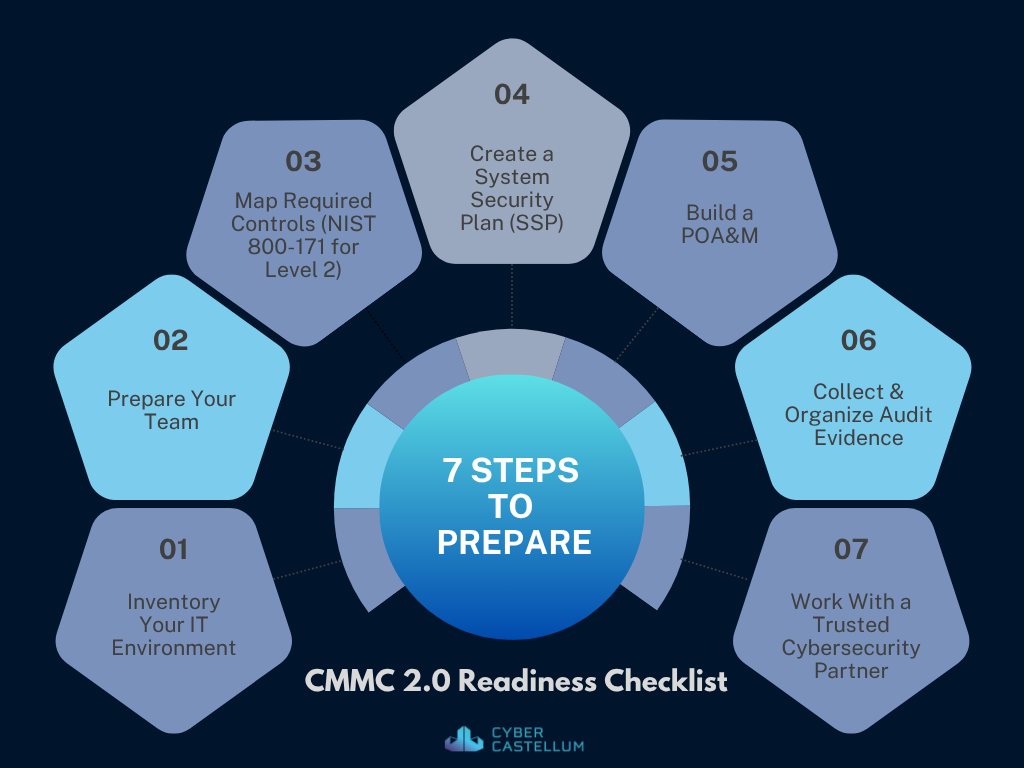
1. Know Your IT Environment
Create an inventory of the systems and software that transmit, store, or process FCI or CUI. This will define the scope of your compliance effort. This should include hardware assets (such as workstations, servers, and storage devices), and software assets (such as business applications, operating systems, security and remote access tools). You also need to document the inventory of users and accounts along with the roles and responsibilities. Other items that should go in the inventory are data assets such as storage devices, network devices such as Firewalls and Virtual Private Networks (VPN), and External Service Providers including any cloud service providers. It is helpful to identify owners that are responsible for the operational and/or security aspects of the assets.
2. Prepare Your Team and Capabilities
As a part of the previous step, you may already have key security individuals involved in the process. However, you need to ensure the complete list of stakeholders is identified, these team members are aware of their roles and responsibilities, and required resources are provided (or budgeted) for. Ensure regular training relevant to individual roles is conducted and records of these training sessions are kept up to date.
3. Review the required CMMC controls
Consider required controls for CMMC level 1 and CMMC level 2 (as relevant to you) and map how your security controls meet these requirements. For example, for level 2, requirements are described in the 14 domains within SP NIST 800-171 (currently, compliance with rev2 is required). Pay close attention to the control objectives specified within each of the controls. It is very important to remember that without meeting all control objectives within each control, your systems cannot be considered compliant with that control.
4. Create a System Security Plan (SSP)
An SSP (System Security Plan) is a required document that describes the systems in your environment handling CUI (Controlled Unclassified Information), the security controls you have in place (based on NIST SP 800-171), how those controls are implemented and maintained, and scope of the assessment. This step should also serve as a sort of gap assessment to determine what you are already doing well and where you need to make improvements.
5. Build a POA&M (Plan of Action and Milestones)
Using the previous steps, build an action plan to remediate any gaps against required controls. The goal is to assign target dates to activities and assign ownership to responsible individuals. This helps to strengthen security controls e.g. implement MFA (multi-factor authentication), encrypt data, secure configurations, and limited admin rights. To get CMMC certified, you need to be able to mark at least 80% of the 110 security controls as Compliant.
6. Collect and Organize Evidence:
Finally, prepare to show “audit artifacts”—logs, screenshots, training records, and system settings. Consider the frequency of security activities performed and related artifacts that need to be preserved. For example, documents such as SSP should have version control and approval dates, vulnerability scans should be conducted according to the frequency defined by the organization, and user access reviews should be conducted in a timely manner. As a part of this step, consider how you will ensure the required evidence is being gathered on an ongoing basis, and how to securely store artifacts. Consider evidence needed from external service providers, especially any cloud service providers that handle CUI. Cloud Service Providers need to be certified at FedRAMP Moderate level – otherwise they will need to demonstrate equivalent security controls during the CMMC assessment.
7. Have a Trusted Partner Guide you
Getting CMMC compliant doesn’t have to be a guessing game—or a massive IT project. Our cybersecurity consulting team specializes in CMMC readiness assessments and support for small to mid-sized DoD contractors. We’ll provide guided remediation support and walk you through any changes needed—from configuring systems to training staff. You can save time and money by skipping the trial-and-error approach. We help you meet requirements faster, reduce rework, and avoid failed assessments that could cost you DoD contracts.
CMMC 2.0 isn’t optional for DoD contractors—it’s becoming a contractual requirement. Whether you’re aiming for Level 1 or Level 2, preparation is the key to staying competitive.
If you’re unsure where to start, don’t go alone.
Ready to get started?
Schedule your free CMMC readiness consultation with Cyber Casllum today and get ahead of the next contract deadline.