
The Ultimate Guide to Cloud Security
Cloud computing has transformed the way organizations store, access, and manage data. However, as cloud adoption soars, so do security risks. Protecting sensitive information in the cloud requires a proactive, multi-layered approach that aligns with industry best practices and regulatory frameworks. In this comprehensive guide, we explore the essentials of cloud security, delve into Cloud Security Posture Management (CSPM), discuss alignment with NIST 800-53 controls, and examine special considerations for FedRAMP compliance.
Understanding Cloud Security: An Evolving Landscape
Cloud security encompasses the technologies, policies, and procedures designed to protect cloud-based assets from cyber threats and unauthorized access. Unlike traditional IT environments, the cloud introduces unique risks such as misconfigurations, insecure interfaces, and shared responsibility models. As a result, organizations must adopt robust security strategies tailored to the dynamic nature of cloud infrastructures.
Cloud Security Posture Management (CSPM): Safeguarding Your Cloud Assets
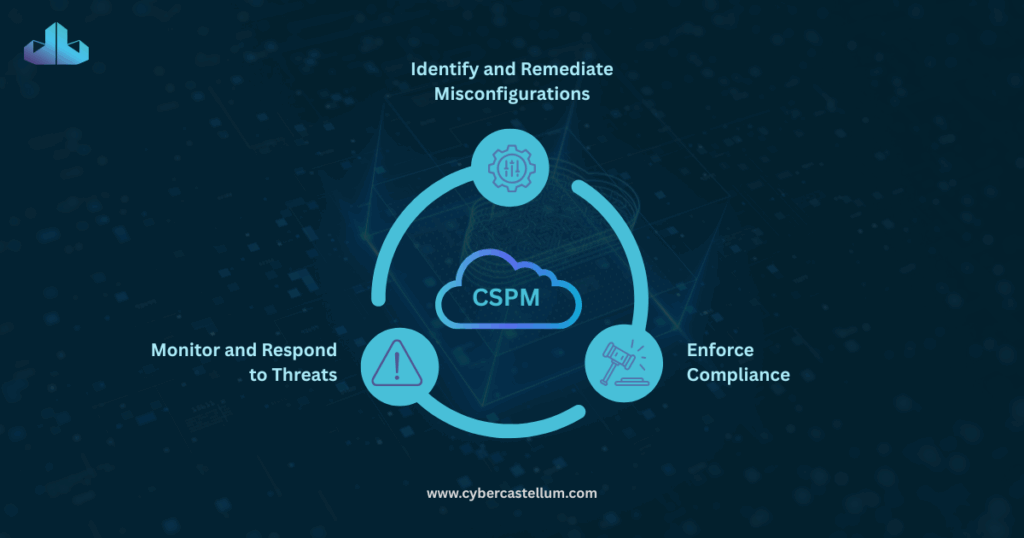
Cloud Security Posture Management (CSPM) is a critical discipline focused on continuously assessing and improving an organization’s security posture in the cloud. CSPM solutions automate the detection of vulnerabilities and misconfigurations across cloud environments, helping organizations:
- Identify and Remediate Misconfigurations: CSPM tools scan cloud resources for security gaps such as publicly accessible storage buckets, improper access controls, and unencrypted data.
- Enforce Compliance: By mapping cloud configurations to regulatory standards, CSPM ensures ongoing compliance with frameworks like HIPAA, GDPR, and PCI DSS.
- Monitor and Respond to Threats: Advanced CSPM platforms offer real-time alerts and automated remediation, reducing the time between detection and response.
By implementing CSPM, organizations gain visibility into their cloud environments and can proactively address security risks before they escalate into breaches.
Aligning Cloud Security Controls with NIST 800-53 and Similar Frameworks
The National Institute of Standards and Technology (NIST) Special Publication 800-53 provides a comprehensive set of security and privacy controls for federal information systems and organizations. Aligning cloud security controls with NIST 800-53 is essential for establishing a strong security foundation and meeting regulatory requirements.
Key Steps for Alignment:
- Map Cloud Provider Controls: Organizations should evaluate how their cloud provider’s native security offerings map to NIST 800-53 controls, such as access control, audit and accountability, and incident response.
- Implement Compensating Controls: Where gaps exist, organizations must deploy additional security measures to meet NIST requirements, such as deploying third-party encryption solutions or advanced logging mechanisms.
- Continuous Assessment: Regular audits and automated scans help verify that cloud configurations remain compliant with NIST 800-53 and similar standards, adapting to evolving threats and organizational changes.
Aligning with NIST 800-53 not only strengthens security but also streamlines the path to compliance with other frameworks, such as ISO 27001 and CIS Controls.
FedRAMP and CMMC Compliance: Special Considerations for Cloud Security
The Federal Risk and Authorization Management Program (FedRAMP) is a mandatory framework for cloud services used by U.S. federal agencies. Achieving FedRAMP authorization requires adherence to stringent security requirements and a rigorous assessment process. Similarly, CMMC complies will soon be mandated for contractors receiving controlled unclassified information (CUI) from the department of defense.
Special Considerations for FedRAMP and CMMC:
- Baseline Controls: FedRAMP and CMMC leverage NIST 800-53 controls, but also impose specific requirements tailored to federal data protection needs. For example, CMMC security requirements are captured in NIST 800-171.
- Continuous Monitoring: Authorized cloud service providers (CSPs) must implement ongoing monitoring, regular vulnerability scanning, and incident reporting to maintain compliance.
- Documentation and Transparency: Detailed System Security Plans (SSPs), security assessment reports, and Plan of Action & Milestones (POA&M) are required to demonstrate compliance and remediation efforts.
- Third-Party Assessment Organizations (3PAOs): Independent assessors play a vital role in evaluating the security posture of cloud offerings seeking FedRAMP authorization or CMMC certification.
Securing FedRAMP or CMMC compliance can be complex, but it opens the door to serving federal clients and demonstrates a commitment to the highest standards of cloud security.
Conclusion: Building Resilient Cloud Security Strategies
In today’s rapidly evolving digital landscape, robust cloud security is non-negotiable. By embracing Cloud Security Posture Management, aligning controls with NIST 800-53 and similar frameworks, and addressing unique requirements in government contracting, organizations can safeguard their data, achieve regulatory compliance, and foster customer trust. Investing in these strategies is essential for navigating the complexities of modern cloud environments and staying ahead of emerging threats.
Frequently Asked Questions:
- What is Cloud Security Posture Management (CSPM)?
CSPM is a set of tools and practices designed to identify and remediate security risks in cloud environments automatically, ensuring continuous compliance and protection against misconfigurations. - Why is NIST 800-53 alignment important for cloud security?
NIST 800-53 provides a comprehensive framework for securing information systems, and aligning with it helps organizations implement industry-recognized best practices and meet regulatory mandates. - What makes FedRAMP different from other compliance frameworks?
FedRAMP is specifically designed for cloud services used by federal agencies, requiring more rigorous security controls and continuous monitoring compared to many commercial frameworks.
For more insights and the latest trends in cybersecurity, contact our experts today!

