Cybersecurity Consulting Firm – Cyber Castellum
Third-Party Risk Management
Why Third-Party Risk Management Is Everyone’s Business In our fast-moving, hyper-connected world, no organization works in isolation. We all rely on vendors, suppliers, cloud platforms, consultants, and other third parties to keep our businesses running. They make it possible to innovate faster, scale without building everything in-house, and focus on what we do best. But […]
Read More
Cybersecurity Recovery & Response: Why You Must Prepare Before a Crisis
When Disaster Strikes, It’s Too Late to Plan: The Critical Importance of Cybersecurity Recovery and Response In the world of cybersecurity, there’s a hard truth that many organizations learn too late: you can’t build your response plan during a crisis. Whether you’re facing a ransomware attack, a data breach, or a system-wide outage, the time […]
Read More
A Practical Guide to CMMC Compliance
Cyber threats are on the rise, and the U.S. Department of Defense (DoD) is taking action to protect sensitive data. That’s where the Cybersecurity Maturity Model Certification (CMMC) comes in; the current version is also referred to as CMMC 2.0. If you’re a defense contractor, understanding CMMC final rule is essential—not just for compliance, but […]
Read More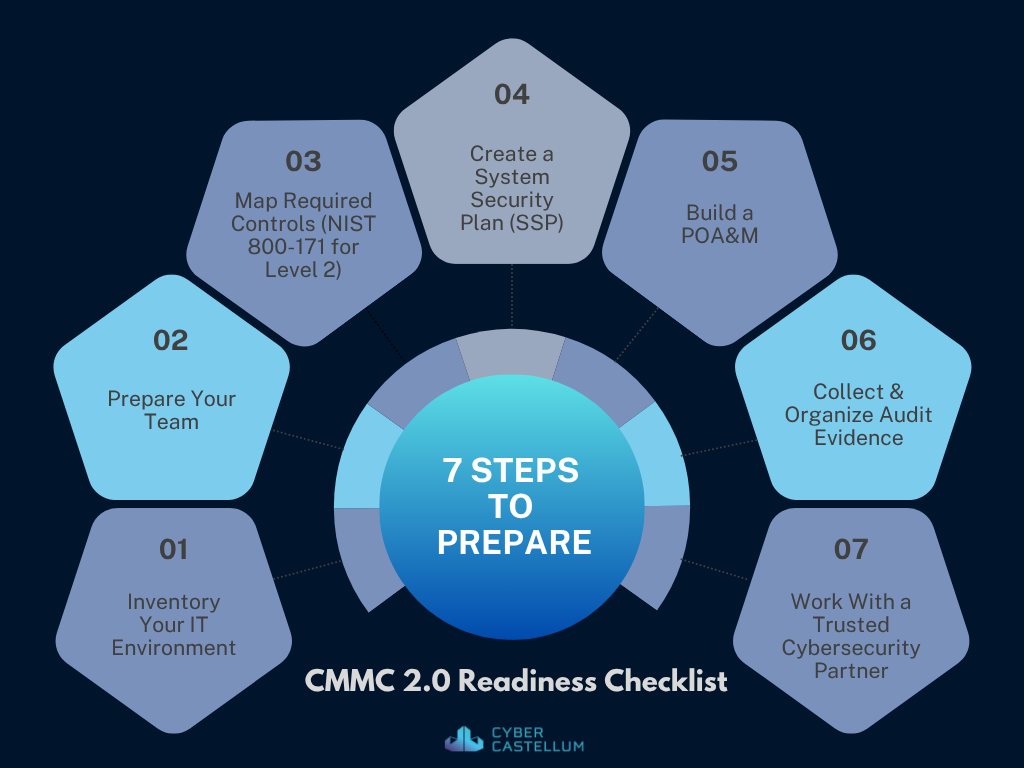
CMMC 2.0 Compliance Checklist for DoD Contractors
If you’re a contractor or subcontractor working with the Department of Defense (DoD), chances are you’ve heard about CMMC 2.0. If your company works on DoD contracts and handles Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), you need to be CMMC compliant. In a previous post Practical Guide to CMMC Compliance, we covered […]
Read More
The Ultimate Guide to Cloud Security
Cloud computing has transformed the way organizations store, access, and manage data. However, as cloud adoption soars, so do security risks. Protecting sensitive information in the cloud requires a proactive, multi-layered approach that aligns with industry best practices and regulatory frameworks. In this comprehensive guide, we explore the essentials of cloud security, delve into Cloud […]
Read More